In an era where digital transactions are king, finding a (Is it safe to transfer money through AEPS) method that is both convenient and secure is paramount. For millions in India, especially those in rural and semi-urban areas, the Aadhaar Enabled Payment System (AEPS) has emerged as a revolutionary way to access banking services. But this convenience brings a critical question to the forefront: Is it safe to transfer money through AEPS? The answer, according to security analysts and banking experts, is a resounding yes, provided users adhere to essential safety practices. Let’s dive deep into the mechanics, security layers, and potential risks to give you a comprehensive expert analysis.
https://example.com/aeps-micro-atm-image.jpg
Alt Text: Is it safe to transfer money through AEPS at a micro-ATM
What Exactly is AEPS? A Quick Primer
Before we dissect its security, it’s crucial to understand what AEPS is. Developed by the National Payments Corporation of India (NPCI), AEPS is a bank-led model that allows you to conduct basic banking transactions using only your Aadhaar number and biometric authentication (fingerprint or iris scan).
Think of it as a “card-less” transaction. Instead of a debit card and PIN, you use:
-
Your 12-digit Aadhaar number.
-
Your bank’s name (as your account is linked to Aadhaar).
-
Your fingerprint, captured by a registered merchant’s biometric scanner.
The primary transactions include balance inquiry, cash withdrawal, cash deposit, and Aadhaar to Aadhaar fund transfers.
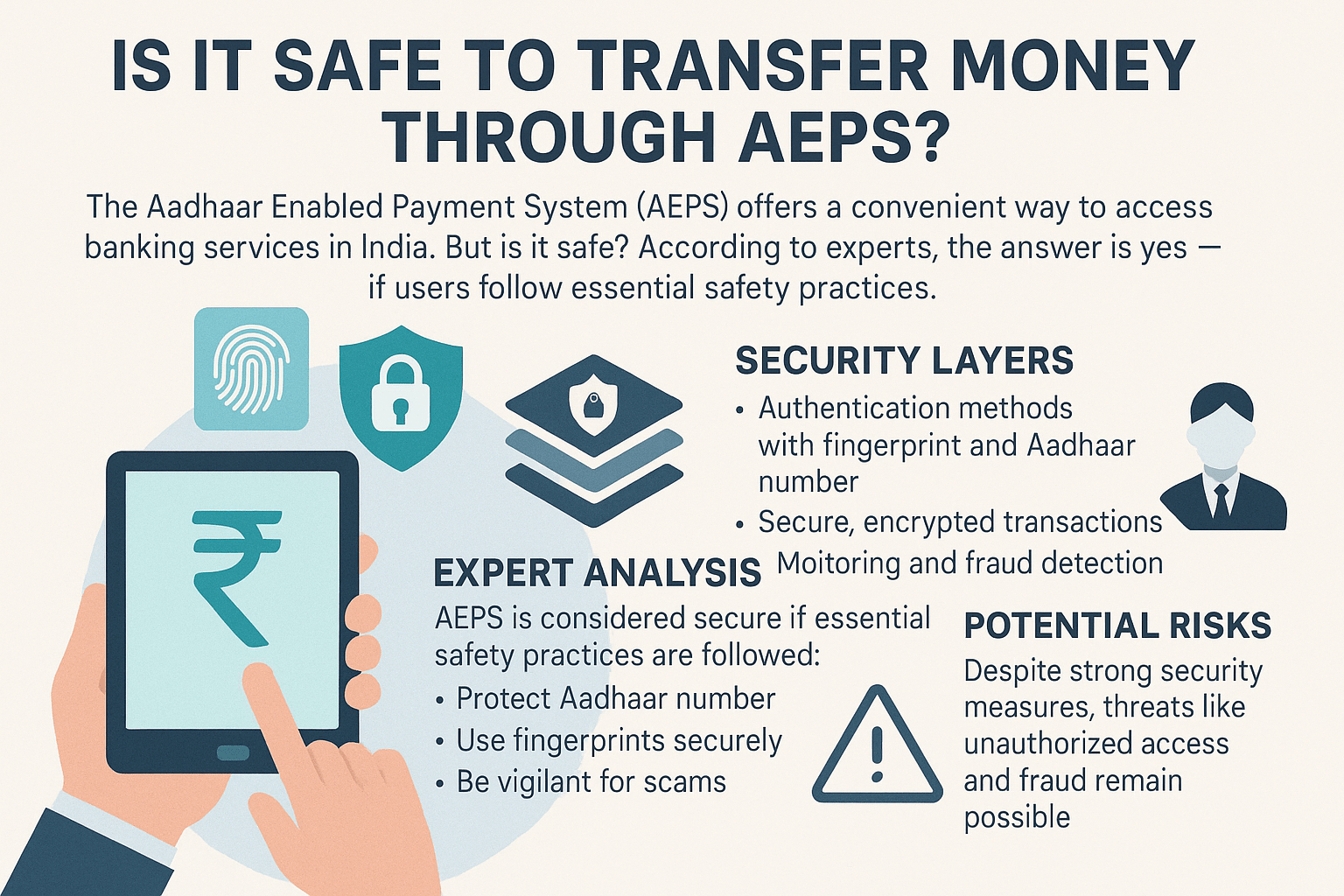
The Fort Knox of Authentication: Why AEPS is Inherently Secure
The core security of AEPS lies in its use of biometrics. This is what sets it apart from other payment methods and forms the bedrock of its safety.
-
Biometric Authentication is Key: You cannot conduct an AEPS transaction without your biometric data. Unlike a PIN or password, which can be guessed, stolen, or phished, your fingerprint or iris scan is uniquely yours. It is incredibly difficult to replicate. This means that even if someone knows your Aadhaar number, they cannot authorize a transfer without you—or more specifically, your physical presence.
-
Minimal Data Entry, Reduced Risk: AEPS requires you to share only your Aadhaar number and bank name. You never enter your bank account number, IFSC code, or debit card details at the point of transaction. This significantly reduces the risk of your sensitive account information being skimmed or stolen by malicious devices.
-
NPCI’s Secure Infrastructure: All AEPS transactions are routed through the secure, robust backend infrastructure of the NPCI. This system is designed to handle millions of transactions daily with multiple layers of encryption and security protocols, ensuring that transaction data is protected in transit.
-
Transaction-Specific OTP (For Some Banks): For added security, especially for fund transfers, some banks have implemented a two-factor authentication process where an OTP is sent to the mobile number registered with the bank account. This adds another hurdle for any potential fraudster.
Understanding the Risks: Where Could AEPS Be Vulnerable?
No system is 100% foolproof, and AEPS is no exception. The risks are not typically in the technology itself but often at the “human” or “endpoint” level.
-
Fake Biometric Scanners: The most significant theoretical threat is a compromised or tampered biometric scanner at a merchant outlet (or Customer Service Point). A malicious device could potentially capture and store your fingerprint data. While this is a complex attack, it is a possibility.
-
Unsecured Communication Channels: If the micro-ATM or the agent’s smartphone uses an unsecured internet connection (like a public Wi-Fi), there is a minor risk of the transaction data being intercepted. However, the encryption used by NPCI mitigates this risk substantially.
-
Misuse by Corrupt Agents: An untrustworthy agent could attempt to make an unauthorized transaction after you have authenticated one. For instance, they might try to process a transfer immediately after your successful balance inquiry, hoping you won’t notice.
-
Aadhaar Number Leakage: Since your Aadhaar number is required, if it has been previously leaked in a data breach, it could be known to bad actors. However, as established, without your biometrics, it is useless for AEPS.

Expert Tips to Ensure Your AEPS Transactions are Safe
Your safety in using AEPS is a shared responsibility between the system’s robust design and your vigilant practices. Here’s how you can fortify your end:
-
Use Only Authorized Banking Correspondents (BCs): Always transact at known, reputable, and authorized outlets. Banks thoroughly vet their BCs. Avoid making transactions at obscure, new, or unverified shops.
-
Verify the Transaction on Screen: Always carefully check the transaction details (amount, type) on the micro-ATM screen before placing your finger on the scanner. Do not proceed if anything looks amiss.
-
Be Wary of Shoulder Surfing: Shield the keypad when entering your Aadhaar number to prevent anyone from seeing it. While the number alone isn’t enough, it’s best to keep it private.
-
Check SMS Alerts Instantly: The moment a transaction is completed, you will receive an SMS from your bank. Read it immediately to confirm the correct amount was debited. If you see an unrecognized transaction, contact your bank without delay.
-
Link Mobile Number and Update Aadhaar Details: Ensure the mobile number linked to your bank account is active and correct. This is crucial for receiving instant alerts. Also, ensure your mobile number is updated in your Aadhaar details through the official UIDAI website or center.
-
Monitor Bank Statements: Regularly check your bank account statements for any discrepancies.
Conclusion: A Secure Tool for Financial Inclusion
So, is it safe to transfer money through AEPS? The expert consensus is clear: yes, it is a highly secure system. Its foundation in biometric authentication makes it one of the safest methods for card-less transactions, particularly valuable for bringing banking services to the fingertips of India’s vast population.
The technology itself is robust and encrypted. The potential vulnerabilities primarily lie at the point of transaction—the merchant and the device. By choosing authorized agents and remaining vigilant during the process, you can effectively eliminate these risks. AEPS represents a powerful and secure step towards true financial inclusion, allowing every Indian with an Aadhaar card to become an active participant in the digital economy.
Frequently Asked Questions (FAQs)
1. What happens if the biometric scanner steals my fingerprint?
This is a complex and rare threat. The UIDAI states that Aadhaar authentication data is not stored by the merchant’s device; it is only used for real-time verification and then encrypted. Furthermore, biometric data is stored in a central repository in an encrypted form, not on individual devices.
2. Can someone transfer money from my account if they just have my Aadhaar number?
No. An AEPS transaction is impossible without biometric authentication. Knowing your Aadhaar number alone is not sufficient to authorize a fund transfer.
3. I didn’t receive an SMS alert for my AEPS transaction. What should I do?
First, ensure your mobile number is correctly linked to your bank account. If the problem persists, contact your bank immediately. The transaction alert is a critical security feature.
4. Is there a daily transaction limit for AEPS fund transfers?
Yes, to minimize risk, NPCI and individual banks impose daily transaction limits on AEPS withdrawals and transfers. The limit can vary from bank to bank but is typically around ₹10,000 for withdrawals. Check with your bank for specific limits.
5. Who do I contact if I notice a fraudulent AEPS transaction?
You must immediately contact your bank’s customer support or visit your home branch to report the transaction. You should also file a complaint with the bank in writing to initiate an investigation.
Disclaimer: This article is for educational and informational purposes only and does not constitute professional financial or security advice. The views expressed are those of the author based on expert analysis and public information. While every effort has been made to ensure the accuracy of the information, we do not guarantee its completeness or efficacy. If you have any concerns about content herein, please refer to our DMCA policy page for guidance on content removal and verification procedures.
